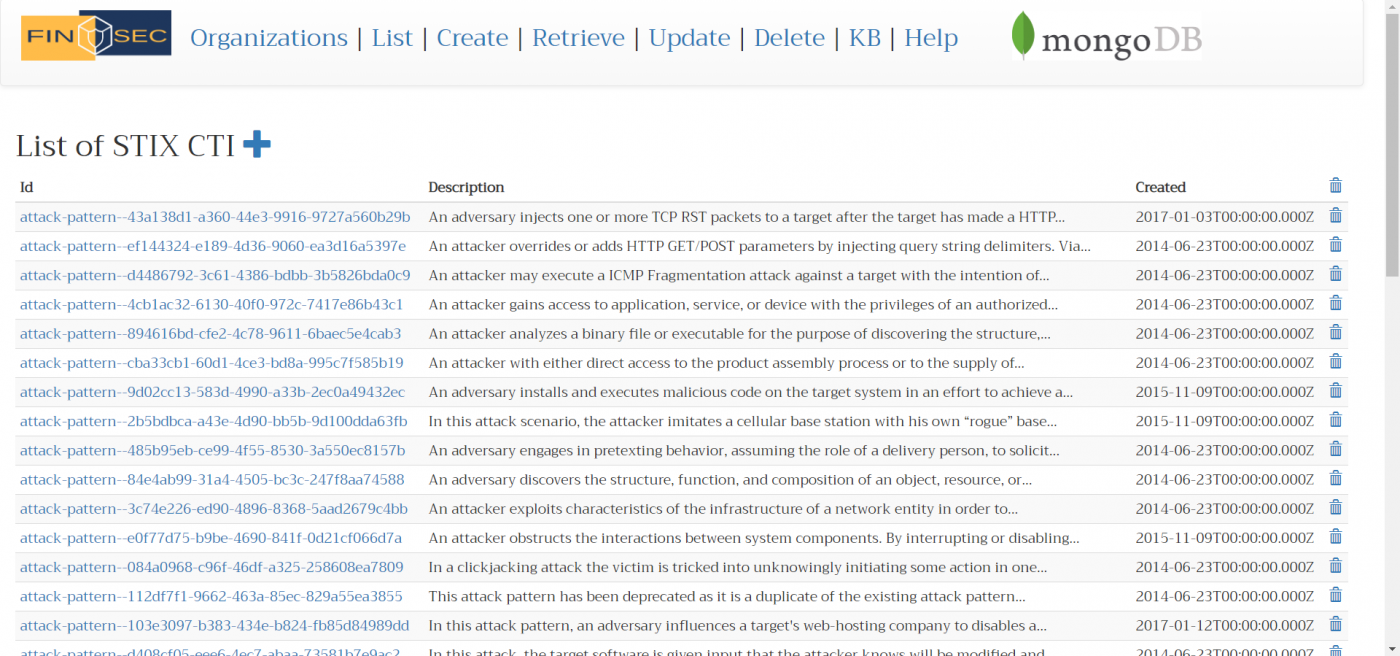
The Security Knowledge Base is a cluster of information gathered from various publicly-available threat intelligence sources, which are external to the FINSEC core platform.
The Security Knowledge Base contains the objects included in the MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) and MITRE CVE (Common Vulnerabilities and Exposures). The content of the Security Knowledge Base is browsable through a visual interface, which at present is included in the Data Tier application. The Security Knowledge Base is a cluster of information gathered from various publicly-available threat intelligence sources, which are external to the FINSEC core platform. The Security Knowledge Base contains the objects included in the MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) and MITRE CVE (Common Vulnerabilities and Exposures). The content of the Security Knowledge Base is browsable through a visual interface, which at present is included in the Data Tier application.
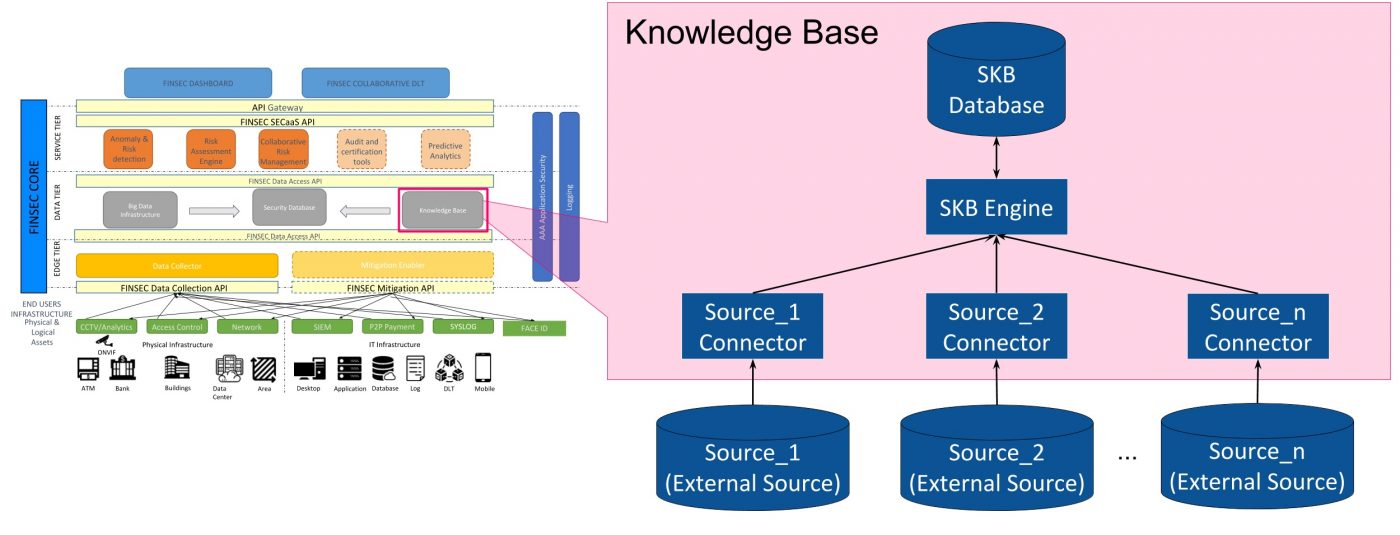
The Security Knowledge Base (SKB) is a module included in the Data Tier of the FINSEC Platform. Its aim is to collect
- Cyber Threat Intelligence coming from external sources of intelligence;
- New Cyber-Physical Threat Intelligence coming from the Service Tier of the FINSEC Platform.
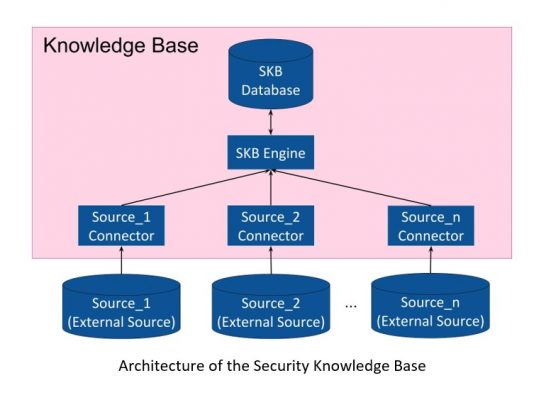
The Security Knowledge Base is a microservice developed in python-flask. As represented in the figure below, it consists of three elements:
- The SKB Database: an instance of MongoDB which stores data;
- The SKB Engine: manages the operations on the SKB Database;
- The SKB Connectors: one for each external source of intelligence. It converts the information coming from the source in FINSTIX format.
Innovation
The mainly novelty of the FINSEC Security Knowledge Base lies in its coverage of both cyber and physical threats for the infrastructures of the financial sector. Specifically, the knowledge base is populated with widely known cyber and physical attack patterns, as well as combinations of threat intelligence involving both cyber and physical threats. Hence, it enables correlation of physical and cyber events and facilitates the discovery of joined/combined attacks against financial infrastructures.
more information
CONTACT 1
Giorgia Gazzarata
CONTACT 1
Ioannis Karagiannis




Reviews
There are no reviews yet.