Financial Supply Chain Security: The value of Collaboration
Information sharing and collaboratively managing and mitigating security issues is the next frontier in financial security.
Recently, an attack to the largest bank of Malta (Bank of Valeta – BOV) was prevented. Hackers attempted to withdraw 13 million euros, but the bank, shut down its systems, closed branches and ATMS and suspended Internet banking. Dealing with this specific attack ended up being successful and the malicious transactions were reversed according to the Prime minister of the country. Although, bank got a severe hit in its reputation.
Another well-known attack, again targeting SWIFT system, took place in February 2016. The attack targeted the Federal Reverse Bank of New Work account belonging to Bangladesh Bank (Central Bank of Bangladesh). In this case the attackers managed to withdraw close to 1 billion dollars and transfer money to Philippines, Sri Lanka and other countries. A big percentage of these transactions were never reversed. Collaboration with all SWIFT peers, other central banks and financial institutions could minimize or even eliminate losses in early stages of the attack.
Early notification of the interested parties can play a huge role in successful dealing with every possible kind of attack since counter actions can be applied much quicker and even before the attack itself. In addition, a seemingly irrelevant sequence of events may have already be recognized as a threat by another institution.
Up until now, the financial supply chain lacks this kind of collaboration. A large number of stakeholders are unwilling to share data and for those who have recognized the importance of collaboration, a unified cyber/physical solution is not developed to support their needs.
Data model standardization
Before realizing the collaboration process, all stakeholders need to conform to a common communication protocol. Thus, the data that will be shared as well as the data model to support messaging and system intelligence has to be defined.
In previous FINSEC meetings and workshops we discussed about the standardization of the data model which will be the backbone of the project. As a result, the first version of FINSTIX was introduced. FINSTIX is a data model based on STIX, with the necessary enhancements to support both cyber but also physical attacks.
New custom Domain Objects were proposed to support the protection of critical infrastructures and provide threat intelligence to FINSEC. (ENISA, 2019) taxonomies were used by FINSTIX as a basis for the modeling of the Threat. FINSTIX specific validation schemas are under development.
Attack scenarios modelling – logical sequence
Since the reference data model (FINSTIX) has almost reached its final form, some real scenarios had to be described using this reference model. The first scenarios that were covered by FINSEC was
§ CCTV camera tampering
§ ATM jackpotting
As it turns out, for this kind of scenarios the modeling of physical or logical areas-of-interest is essential. These are the areas that each probe will be responsible of monitoring. Thus, they have to be strictly defined. The format of the Events produced by each probe, as well as the message format for configuring the probe itself are also provided.
For the specific case of the ATM jackpotting, we can identify a number of physical/logical areas-of-interest. Some of them are referring to the ATM itself and others to the room, entrance areas, printer area or any other area that can be monitored by a system Probe.
SILO provided an example of how ATM jackpotting can be modelled using the FINSTIX approach. All pilot scenarios will be modelled using the FINSTIX reference model.
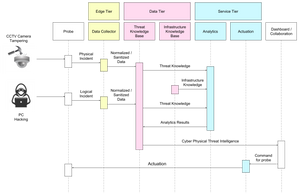

Figure 1: CCTV camera tampering – logical flow
Figure 1 illustrates a simple CCTV camera tampering scenario. In this scenario, a Probe identifies a physical event (CCTV camera tampering) and it sends normalized data to upper layers of FINSEC. The Data Collector normalizes/sanitizes the incident gathered from the Probe and sends it to the Threat Knowledge Base. Then, the Predictive Analytics module collects and processes the knowledge coming from the Threat Knowledge Base and the Infrastructure Knowledge Base.
The Knowledge base identifies that camera tampering may be associated with other incidents (e.g. hacking CCTV analytics software is frequently coexisting with tampering) and mitigation actions are applied. Probe configuration messages may be sent back to the Probe (e.g. send data in higher rate).
All the messages for this scenario have to be FINSTIX compatible.
Information Sharing – Possible solutions
When a FINSEC probe produces a new event, incident or alarm, analytic tools will check against the Knowledge Base and will detect Threats or Risk level changes. In case the Organization identifies an attack that may influence another stakeholder, it has to share information across its boundaries. Sharing information, with dependent stakeholders, is a key factor for a collaborative security project like FINSEC.
An Organization may share information about attacks, mitigation actions, updates, new assets or services, regulation violations etc.
Information sharing techniques like block chain solutions and platforms-protocols like TAXII and MISP are under investigation.
While (TAXII, 2018) and (MISP, 2016), have already a well-known structure, building a block chain ledger to support FINSEC’s needs in the financial sector needs is not trivial.
For the specific option of a decentralized application (DApp) based on block chain, FINSEC partners are working on possible implementations using ‘Truffle Suite’.
(TRUFFLE SUITE, 2019) is a developing environment that enables testing framework and asset pipeline for blockchains using the Ethereum Virtual Machine (EVM).
Truffle Suite was selected for its simplicity and the out the box capabilities it provides for testing. Nevertheless, the final block chain approach will be based on a mature consortium using as guide projects like ‘Hyperledger’ and ‘Quorum’.
Another key point is the sanitization before sharing any piece of Information. This process will also be covered in the scope of FINSEC’s information sharing approach.
Future work includes the standardization of Information sharing that will be described and disclosed to all partners.
Eventually, FINSEC Organizations will use the tools and techniques provided, to collaboratively mitigate all kinds of security issues in the financial supply chain.
By Kostantinos Mavrogiannis, Singular Logic
References
ENISA. (2019, January 28). ENISA. Retrieved from ENISA: https://www.enisa.europa.eu/publications/enisa-threat-landscape-report-2018
MISP. (2016). MISP. Retrieved from MISP: https://www.misp-project.org/
TAXII. (2018). TAXII. Retrieved from TAXII: https://oasis-open.github.io/cti-documentation/
TRUFFLE SUITE. (2019). Retrieved from TRUFFLE SUITE: https://truffleframework.com/

